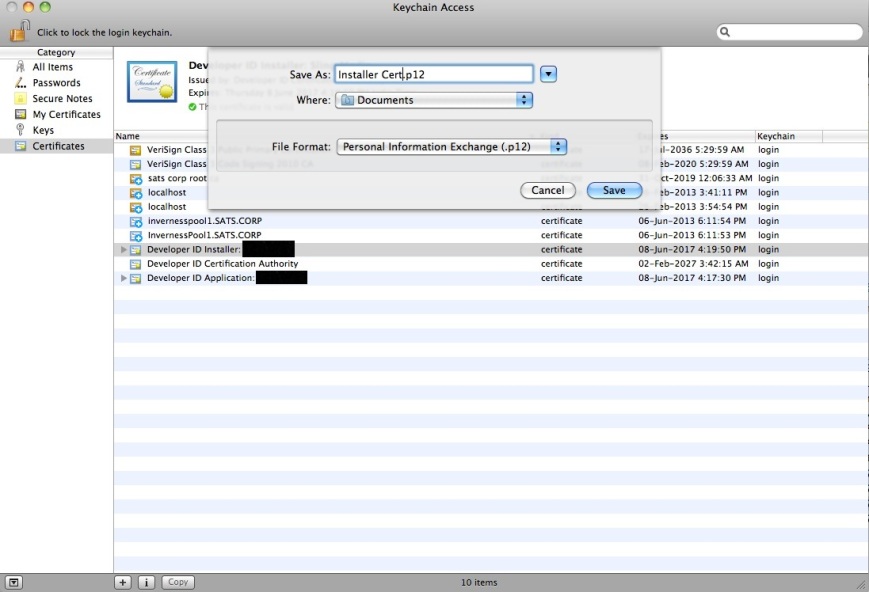
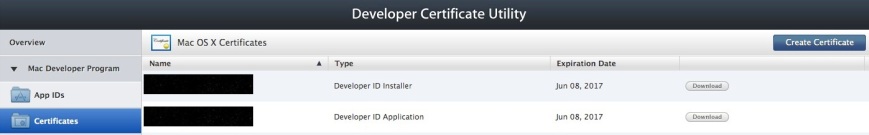
This is the first in a series of 3 posts documenting the working of Gatekeeper and signing of the plug-ins and the installers.
Gatekeeper is Apple’s security feature that is designed to protect Mac OS X users from malicious software.
Gatekeeper will be able to run in three modes:
1. Mac App Store: The default mode, a stricter mode in which users will only be able to install applications downloaded from the Mac App Store.
2. Mac App Store and identified developers: Relaxed mode that allows users to install applications downloaded from the Mac App Store or identified developers (Applications signed using certificate generated by Apple.)
3. Anywhere: Any application can be installed.

Gatekeeper options
While option 1 is the safest, option 3 is like being back on Lion or any other previous version of Macintosh. Option 2 seems like a good middle path which quite a few developers will take.
Important points to remember regarding Gatekeeper:
1. The Gatekeeper does not check or restrict Plug-ins, Frameworks etc.
2. Any software already installed—and that has been run at least once—will continue to run even after Gatekeeper is enabled. Gatekeeper checks on first launch of an application.
3. Gatekeeper uses OCSP (Online Certificate Status Protocol) to verify the certificate, OCSP talks to servers over the Internet.
4. Gatekeeper validates/checks all the installer.
For more information on Gatekeeper behaviour refer: Macworld article and tidbits article
I did few experiments to understand the Gatekeeper better.
Check 1: Downloaded a pkg installer (unsigned) on 10.6 and ran it on 10.8 from a pen drive
I Downloaded a pkg installer which doesn’t work (not signed) on 10.8 (Mountain Lion) on 10.6 (Snow Leopard) using Google Chrome and transferred it to a pen drive next day and tried installing it. The Gatekeeper detected that the pkg was not signed. The behavior was same when I downloaded the installer from a mail server.
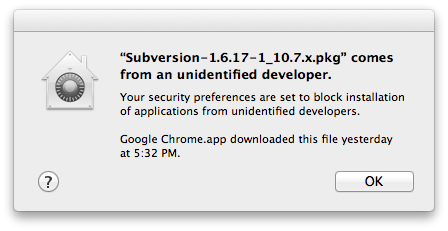
Downloaded on Snow Leopard but Gatekeeper detected it.
Check 2: Downloaded a pkg installer (unsigned) on 10.8
I Downloaded an pkg installer which doesn’t work (not signed) on 10.8 on 10.8 and tried installing it again Gatekeeper was up to the task. The behavior was same when I downloaded the installer from a mail server.
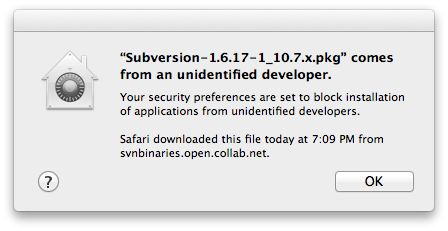
Check 3: Downloaded a signed pkg installer on a fresh 10.8 machine without internet
Basically this machine had Mountain Lion Preview 4 and my signed installer was not used on this machine. I pulled out the LAN cable (WiFi was turned off) and I tried to install my package using the pkg installer. Gatekeeper allowed the installer to run without any warning. Looks like OCSP (Online Certificate Status Protocol) is not the only check Gatekeeper performs. Good news is that Gatekeeper doesn’t need the machine to be connected to internet for it to verify the certificates. The behavior was same when I downloaded the installer from a mail server.
Check 4: Downloaded an application (unsigned) on 10.6 and ran it on 10.8 from a pen drive
The application didn’t have a pkg installer. I just had to drag and drop the app into “Applications” folder. Copy worked fine but when I tried to launch the application, Gatekeeper kicked in. I used an older version of TextWrangler to generate the issue.
Check 5: Downloaded an application (unsigned) on 10.8
Same as Check 4. Gatekeeper wouldn’t allow me run the application. I used an older version of TextWrangler to generate the issue.

Check 4 and 5
Check 6: Downloaded a signed application on a fresh 10.8 machine without internet
Gatekeeper verified and allowed the application to launch.
Gatekeepers doesn’t quite meets my expectation. I would be very happy if it starts validating frameworks, plug-ins and command line tools that the user can download from internet. There are already improvements in Gatekeeper implementation in Mountain Lion GM over Mountain Lion Preview 3. But it is a good start none the less.